Cyber-security puzzle: Who is sending Internet traffic on long, strange trips?
Loading...
Data streams from US financial companies and foreign governments sent out over the Internet are being rerouted by computer hackers – diverted to overseas locations where they can be spied upon or altered, then shot along to their expected destination with barely a delay and nobody the wiser, cyber-security experts say.
Victims whose Internet traffic was diverted included major US financial institutions, network service providers, and foreign governments including South Korea, Germany, the Czech Republic, Lithuania, Libya, and Iran.
Beginning in February and then again in August, Internet data streams were redirected almost daily – with different entities targeted sometimes over multiple days – according to Renesys, a cyber-security company in Manchester, N.H., that specializes in monitoring Internet pathways.
In each case, the intentional diversion sent the company or government data stream cascading overseas to a distant location – then quickly on to its expected destination in less than a second – with nobody noticing. Well, almost nobody.
Doug Madory, a Renesys expert, is one of the few able to see what was going on. As he watched his computer monitor in late summer, he says, unidentified hackers subtly diverted a US Internet provider’s Denver data stream – its e-mails and electronic file transfers – that were intended to travel just across town to another Denver location.
“Route hijacking has been around for a long time, but it’s typically been accidental, brief, and highly public,” Mr. Madory says. “What we’re seeing now is subtle, almost impossible to detect – a man-in-the-middle setup to intercept data over relatively long periods of time: several hours or even an entire day. It looks like a targeted attack by either a criminal organization or nation state.”
Typically the Denver data would follow the cheapest, if not most direct, path over the Internet via fiber optic lines, routers, and servers to Dallas, then to Kansas City, then back to Denver, Madory says. Out of the way, but not unduly so.
But what he saw in August was the Denver data instead skipping more than 3,600 miles from Chicago to New York and on to London – then finally to an Internet service provider (ISP) in Reykjavik, Iceland.
That wasn’t the end of the trip. From there, the Denver data shot 3,600 miles back to the US via transit points in Montreal, Chicago, Kansas City – and at last to its intended destination just across town in Denver. The entire 12-stop trip took just two-tenths of a second – about one-tenth longer than usual.
It was not enough of a delay for most people to notice. Yet during its visit to Iceland, the Denver data stream could have been copied or tampered with, Madory and other experts say.
The phenomenon is called Border Gateway Protocol hijacking, or BGP hijacking. Until now such occurrences have been very brief – just a few minutes until the problem is detected.
In one example, Pakistani authorities, angry over an anti-Muslim video posted on YouTube in February 2008, ordered the nation’s telecom provider to cut access to the YouTube site. But instead of blocking YouTube access just in Pakistan, the fake Internet address that technicians used to “hijack” traffic to the site leaked to ISPs outside the country – blocking YouTube worldwide for about two hours.
In 2010 a Chinese ISP momentarily hijacked about 10 percent of all Internet traffic, including data that should have gone to CNN, Dell, Apple, and Starbucks but was mistakenly sent to China instead. The incident lasted for just minutes, and the ISP said it was an accident caused by the misconfiguration of its system.
But the recent, extremely subtle attacks detected by Renesys were conducted over many hours or even a day or more – and look a lot like a classic “man-in-the-middle” cyber-espionage attack in which a victim organization never sees its data being intercepted en route to its intended destination, others agree.
“This looks like a sophisticated approach probably only available to elite hacktivists, criminal groups, and nation states,” says Richard Bejtlich, chief security officer for Mandiant, based in Alexandria, Va. “If you can do a man-in-the-middle attack, then you can get access to people’s banking credentials. So it’s probably most interesting to criminal organizations.”
Intelligence organizations in Russia and China might be interested, although the National Security Agency perhaps less so. The NSA already has direct access to fiber optic cables worldwide, according to documents leaked by Edward Snowden, the former NSA contractor.
“China and Russia are well instrumented inside their borders, but when they want access outside they have to do these kinds of tricks, so that might be what we’re seeing,” Mr. Bejtlich says.
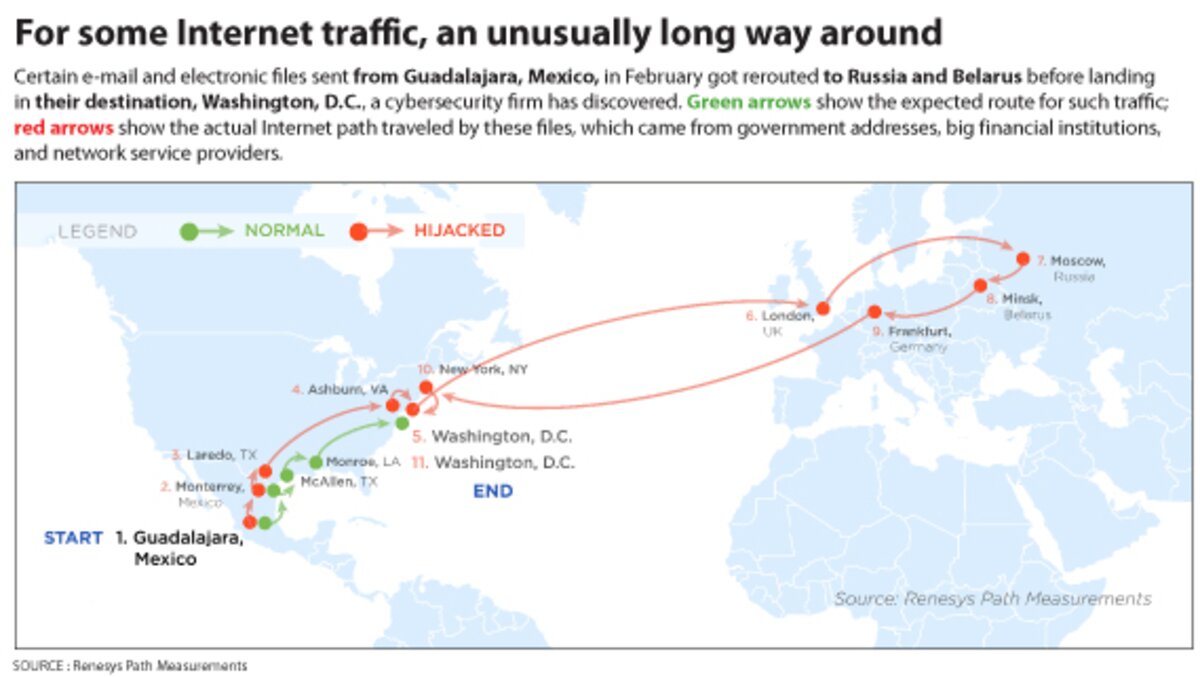
In February, Madory and other experts at Renesys observed a sequence of subtle but unusual events lasting up to several hours. The redirections of Internet data took place almost daily during the month, with victim networks changing daily.
In each case, governments, US financial institutions, and network service providers worldwide had their data quietly redirected, first to Moscow, then finally to the Belarusian ISP GlobalOneBel – and then sent onward to the intended destination.
“We saw it start off looking like a criminal operation, targeting the financial companies,” Madory says. “The next day we saw it targeting foreign governments, so we thought maybe it’s a nation state. Now it’s not clear whether this group was a government or a criminal operation.”
On one day in February, Madory says, traffic from many places around the world was redirected to Belarus. In one example, data sent from Guadalajara. Mexico, to Washington, D.C., would have traveled 6,535 miles through Moscow to Belarus – then on to its destination in Washington. That hijack took about 238 milliseconds – about a quarter of a second for the data to arrive at its proper locations – compared with about a tenth of a second if the data had not been diverted. Humanly imperceptible, Madory says.
It’s not clear whether the ISP operators in Belarus or Iceland were participants – or whether someone just hacked their network, he says. Other experts who haven’t seen the data are circumspect.
“Whether this specific incident was intentional or not, cases like this do typically have a negative affect on the victim,” writes Andree Toonk, founder and lead developer at BGPmon Network Solutions, another firm that tracks BGP attacks and hijacking, in an e-mail.
“It's also not hard to imagine what the possibilities are when trying to set up an attack like [this] with bad intentions.”