Influencers oppose expanding federal hacking authorities
Loading...
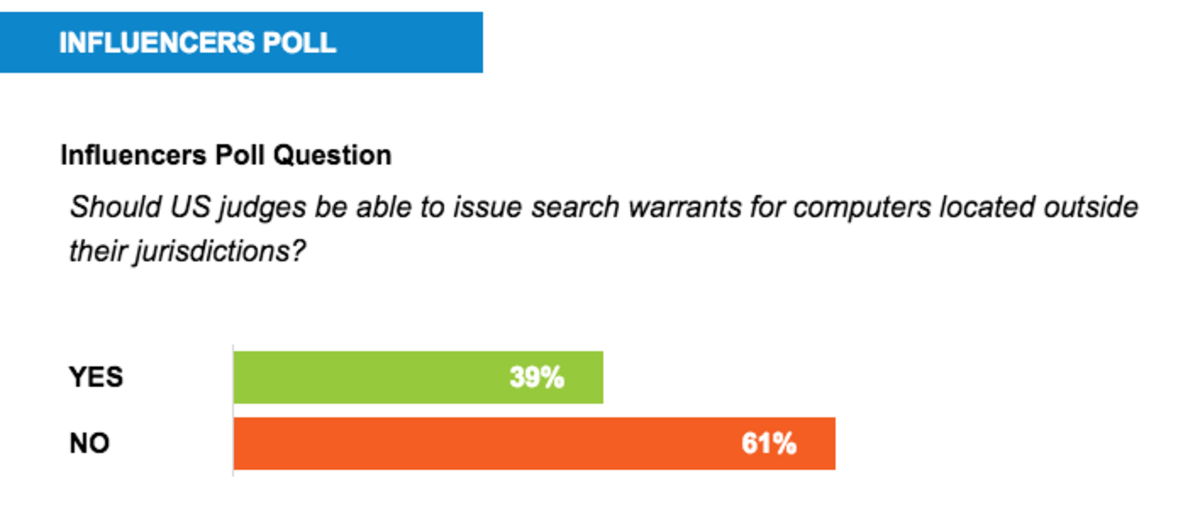
Nearly two-thirds of Passcode’s Influencers said US judges should not be able to issue search warrants for computers located outside their jurisdictions.
In late April, the Supreme Court����a controversial change to Rule 41, a relatively obscure federal criminal procedural rule, that would allow US magistrate judges to grant law enforcement warrants to search computers outside their home districts.��
The Justice Department has long been pushing for this change as it grapples with the challenge of investigating Internet crimes that don’t conform to geographic borders: Agents, they say, should be able to search computers in multiple locations under a single warrant or even when they don’t know exactly where the device is physically located, without being vulnerable to legal challenge. Otherwise, law enforcement officials worry that criminals will be able to exploit digital tools such as the Tor anonymous browser to conceal their true locations and escape prosecution.
But a majority of security and privacy experts from across government and the private sector surveyed by Passcode worry the rule change may dramatically expand the FBI’s digital surveillance powers without much oversight or public debate, as even the lowest-ranking US judges couldconceivably grant the FBI the ability to hack computers anywhere in the country or even the��world.
“As with the recent encryption debate, remote hacking is not something that one court or magistrate judge should have to decide in isolation,” said Abigail Slater, vice president of legal and regulatory policy at the Internet Association, a political lobbying organization for the Internet industry. “The issue deserves a robust national��debate.”
Unless Congress acts upon the proposal, the rule change will automatically become law. Any bill proposed by the members of Congress who want to stop the rule changes, such as a proposal from��Sen. Ron Wyden (D) of Oregon, would need to clear both houses of Congress and get President Obama’s signature before the beginning of December to have any��impact.
Several Influencers worry the rule change could set a dangerous precedent that disregards differences in laws around the country – and the world. “Judges operate – or should operate – within their own jurisdictions, period,” said one Influencer who chose to remain anonymous. “The notion that a judge sitting somewhere in the US can issue a warrant for outside the US is not only contrary to international law but shows a contempt and disregard for the laws of other jurisdictions.”��
Civil liberties groups and major technology organizations, another Influencer added, “are right to question the constitutionality of this ruling. It is dangerous to allow any government carte blanche such liberal access to thousands and even millions of computers globally.” To preserve the candor of their responses, Influencers have the option to answer the survey on the record or anonymously.
This issue has picked up steam since a district judge in Massachusetts ruled in April��that a warrant obtained by FBI investigators from a magistrate judge in Virginia����outside that district found to have visited the child pornography site Playpen. It was hosted on Tor, the anonymous Web browser, which bounces users’ traffic among multiple servers to make it harder to track identifiable information.
Yet these kinds of federal criminal investigations can also ensnare foreign citizens: The FBI also hacked����in Denmark, Greece, and Chile last year. Since the rule change could allow federal judges to issue search warrants for computers outside the US, other Influencers worried that other countries may take similar steps��– raising a whole host of questions about whether there could be repercussions for American citizens.
“A related question is if a Chinese, Russian, EU, Saudi, Ecuadorian, or other judge can issue warrants for computers outside their jurisdiction. After all, what’s sauce for the goose is sauce for the gander,” one Influencer said. “Then this brings up the question of if there is such a thing as jurisdiction, if a judge can act anywhere.”
Or, as Günter Ollmann, chief security officer at Vectra Networks, a San Jose, Calif.-based cybersecurity company, said: “Would the US be bound to honoring foreign governments the same jurisdictional incursion into US computers?”
Since cases surrounding Tor’s Web browser helped prompt the proposed rule change, other Influencers worry that expanding the government’s hacking authorities this way could jeopardize the rights or even safety of people, such as activists or journalists, who depend upon the service. “If this ruling stands, magistrate judges could seize and search any devices outside their local authority if the target is using anonymity software such as Tor, which protect the privacy rights of many good people who require anonymity for good reasons,” one Influencer��said.
Still, a 39 percent minority of Influencers said that judges should be able to issue hacking warrants beyond their jurisdiction – especially since it’s not always easy to track the location of criminals on the Web. “In the Internet age, the location of computers can’t always be determined with certainty,” said Stewart Baker, a partner at the Washington-based law firm Steptoe & Johnson. “We shouldn’t give criminals safe haven from search just because of uncertainty about their location.”
Ultimately, given the ability of criminals and child pornographers to use Tor and other hidden services to keep their cover, “this interpretation of the law is a requirement when we live in a digitally connected world, where bad things happen under cover of anonymized traffic,” said Jeffrey Carr, president and CEO of Taia��Global.
Hackers are smart enough, adds Jenny Durkan, a Seattle-based attorney at the law firm Quinn Emanuel, “to set up shop in places they cannot be touched, to erase drives if they think they are detected or otherwise avoid being caught. Investigations must be able to gather this kind of evidence, using modern capabilities.”
Since the Internet itself is “borderless,” others said, the law must keep up. “Many of the same activists who claim the Internet is ‘borderless’ will take the opposite position when it comes to judges, keeping them limited to their own jurisdiction,” said Jason Healey, senior researcher at Columbia University’s School of International and Public Affairs. “Hopefully this will empower the most digitally smart��judges.”
However, Mr. Healey wants to be sure US judges do not misuse their new powers. “We need to keep watch to see if law enforcement does indeed rely on these digitally aware judges, or actually [turns to] the digital dummies in order to assert more��power.”
What do you think?����of the Passcode Influencers Poll.
Who are the Passcode Influencers? For a full list, check out our��
Comments:
NO
“This question can’t be answered separately from the broader question of whether or not US judges should be able to issue hacking warrants (or ‘remote access search’ or ‘network investigative technique’ warrants) at all, and if so, under what procedures. That’s a question that has never been publicly asked or answered by policymakers. Therefore my answer is no – US judges shouldn’t be able to issue extraterritorial hacking warrants, until Congress and/or higher courts actually consider the very difficult constitutional and policy questions that surround the practice of government hacking, a practice that raises even more unique privacy and security concerns than wiretapping does but unlike wiretapping lacks any clear Fourth Amendment or statutory framework to control those risks. And even if we conclude that courts should be able to issue extraterritorial hacking warrants, it should be Congress making that decision, not an obscure judicial advisory committee via a change to the federal rules of criminal procedure. This is not a merely procedural question but represents a substantive change in law that requires sustained investigation and debate by our elected lawmakers.”��– Kevin Bankston, Open Technology Institute
“I think this question answers itself. ‘Outside their jurisdiction’ pretty much says it all. Judges can issue all the warrants they want for stuff outside their jurisdiction but don’t expect anyone to obey them and good luck enforcing them.”��– Space Rogue, aka Cris Thomas, Tenable Network Security
“The entire rationale for judicial jurisdiction is predicated upon demarcation amongst judicial districts. Undermining this independence will create an untold array of problems that harm the foundation undergirding rule of law.”��– Sascha Meinrath, X-Lab
“Law enforcement agencies have never sought or received hacking authority from Congress. The rule 41 changes are an attempt to sneak through an expansion of authority.”��– Christopher Soghoian, American Civil Liberties Union
“Until a uniform set of standards is established for the collection of digital information, such extra-jurisdictional actions run a significant risk ��of setting precedents that may conflict or preclude the development of more universal standards.”��– Influencer
“Remote access searches, conducted via government hacking, is dangerous, especially without specific legislative safeguards. Despite this, the questions inherent to remote access searches and government hacking have never received a proper public debate or discussion. Absent that debate, the Department of Justice should not be able to grant themselves that authority.”��– Amie Stepanovich, Access
“Civil liberties groups and major technology organizations are right to question the constitutionality of this ruling. It is dangerous to allow any government carte blanche such liberal access to thousands and even millions of computers globally. Under Rule 41 there were limitations. If this ruling stands, magistrate judges could seize and search any devices outside their local authority if the target is using anonymity software such as Tor, which protect the privacy rights of many good people who require anonymity for good reasons.”��– Influencer
“No. U.S. judges shouldn’t be mucking around in foreign affairs.”��– Influencer
“It should be an acceptable practice for the sole purpose of locating a computer so that the appropriate compulsory process can be obtained from the jurisdiction where it is determined to be located.”��– Influencer
��
YES
“The ugly truth: In a borderless world, it is logically equivalent to say that (1) you are outside all jurisdictions, and (2) that you are inside all jurisdictions. ��The former is a world without accountability. ��The latter is a one-world juristocracy. ��The only way to preserve the status quo ante of limited jurisdictional reach is total attributability of all cyber actions, i.e., zero anonymity.”��– Dan Geer, In-Q-Tel
“Unlike current policy, there should be a presumption of using the Mutual Legal Assistance process, with broader warrants only where that cooperative process has been exhausted.”��– Peter Swire, Georgia Institute of Technology
“The question as posed is a bit overly broad. Enabling judges to issue search warrants for any device outside their jurisdiction as a default seems like a bad idea (jurisdiction exists for a reason), but in the specific case where the device can’t be located, it may make sense to have a limited exception permitting issuance by (for example) the DC court or a court with jurisdiction over a victim. The process would need safeguards to limit the consequences of an unintentional international search and prevent forum shopping. The difficulty of locating networked devices means that not having such an exception creates an oddly perverse incentive by rewarding criminals that can conceal the location of their devices.”��– Influencer
“The FBI’s lamentable anti cyber-crime efforts, stymied by their own lack of resources but bolstered by their insistence on being the pre-eminent cyber investigative organ, protect all but the most high-profile or embarrassing cyber criminals. This bill would facilitate a true effort by local, county and state law enforcement to pursue and capture cyber criminals, and introduce risk into the highly lucrative world of cyber crime.”��– Nick Selby, Street Cred Software
“Judges have already been doing this for years. ��Remote e-discovery is quite common. ��In those cases, if a court has jurisdiction over a party and that party has access to data anywhere, the party has always been obligated to comply. ��That said, foreign laws should be taken into account more than they have been in the past (e.g., Microsoft data in Ireland).”��– Influencer
“Law enforcement may need to access an Internet connected computer to perform a reasonable search with probable cause even though they are unsure of the computer’s precise location. There needs to be a procedure for a warrant to be issued in that circumstance. ����The more interesting change that is being proposed to federal criminal procedures would allow law enforcement to use a single warrant to access large numbers of computers located in different jurisdictions that have been ‘damaged without authorization,’ such as in the case of a botnet. There are times when government authority may be useful to protect the Internet from botnets. For example, a large distributed denial of service botnet with a peer-to-peer command and control channel that couldn’t be shut down could pose a significant threat to the stability of the Internet. With lawful authority, it might be possible to disable the nodes of such a botnet so that they no longer posed a threat. However, any anti-botnet operation that tampers with the computers of innocent victims needs to be executed with great caution. Overzealous anti-botnet operations have negatively impacted the rights of innocent users in the past. Careful oversight of these kinds of operations is needed to ensure that third party interests are given the consideration they deserve, and the rule change being proposed here does not provide for that sort of oversight mechanism.”��– Tom Cross, Drawbridge Networks
“When a crime is committed over the Internet and the search of the data can be performed over the Internet then the concept of location becomes less meaningful for a criminal investigation.”��– Influencer
“My answer of ‘yes’ is based on assumption that such power would only be used for circumstances where the location is technically indeterminable, not a carte blanche for forum shopping.”��– Influencer
“Hackers are smart enough to set up shop in places they cannot be touched, to erase drives if they think they are detected or otherwise avoid being caught. ��Cyber criminals are a significant threat to our personal privacy, our national security and our economy. Investigations must be able to gather this kind of evidence, using modern capabilities. ��Constitutional rights and personal privacy must be protected. But this happens not by letting bad guys go, but by judges exercising strict oversight of the both the issuance and execution of search warrants. ��Courts already have deep experience in balancing these interests. ��There are many measures courts can take to protect the interests of innocent third parties.”��– Jenny Durkan, Quinn Emanuel
What do you think?����of the Passcode Influencers Poll.
��