All Passcode
 Ashley Madison breach a painful reminder of online data's permanenceThe apparent perpetrator behind the Ashley Madison leak claimed the attack was over the company's treatment of sensitive user data. But experts say that data shared with Web companies rarely ever goes away.
Ashley Madison breach a painful reminder of online data's permanenceThe apparent perpetrator behind the Ashley Madison leak claimed the attack was over the company's treatment of sensitive user data. But experts say that data shared with Web companies rarely ever goes away. Opinion: Why the information sharing bill is anti-cybersecuritySupporters of the Cybersecurity Information Sharing Act says it's an essential tool for Washington and industry to exchange threat intelligence. But in reality, it would give the government carte blanche to collect and store more data on Americans, putting everyone's information at greater risk.
Opinion: Why the information sharing bill is anti-cybersecuritySupporters of the Cybersecurity Information Sharing Act says it's an essential tool for Washington and industry to exchange threat intelligence. But in reality, it would give the government carte blanche to collect and store more data on Americans, putting everyone's information at greater risk.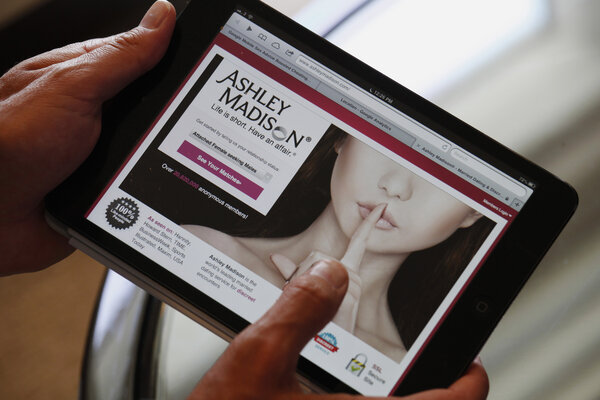 Opinion: Ashley Madison hack reveals need for new approach to guard intimate dataAfter its users' data was exposed online, Ashley Madison issued copyright takedown notices to have it removed. It's a bad use of copyright law but reflects a troubling legal environment where digital media companies own users' most personal images and information.
Opinion: Ashley Madison hack reveals need for new approach to guard intimate dataAfter its users' data was exposed online, Ashley Madison issued copyright takedown notices to have it removed. It's a bad use of copyright law but reflects a troubling legal environment where digital media companies own users' most personal images and information. Opinion: The value of unmasking Tor's dark sideThe identity shrouding Tor browser is a godsend for many people – including criminals – trying to avoid detection online. But using it doesn't erase everyone's digital footprints, giving researchers many clues for hunting down Tor's more nefarious users.
Opinion: The value of unmasking Tor's dark sideThe identity shrouding Tor browser is a godsend for many people – including criminals – trying to avoid detection online. But using it doesn't erase everyone's digital footprints, giving researchers many clues for hunting down Tor's more nefarious users. Cybersecurity pros makes final push to quash proposed export restrictionsInstead of the Commerce Department plan to limit the export of surveillance technology, many industry professionals and experts want entirely new proposals.
Cybersecurity pros makes final push to quash proposed export restrictionsInstead of the Commerce Department plan to limit the export of surveillance technology, many industry professionals and experts want entirely new proposals. Social media reports of 'hacked' Groupon accounts on the riseThis month alone nearly 30 customers have tweeted that their Groupon accounts have been compromised or "hacked." The company has denied any data breach.
Social media reports of 'hacked' Groupon accounts on the riseThis month alone nearly 30 customers have tweeted that their Groupon accounts have been compromised or "hacked." The company has denied any data breach. Opinion: Hacking Team breach a gold mine for criminal hackersWhile the breach at the Italian spyware firm shines a light on the shadowy world of surveillance technology, it has also made the Web a much more dangerous place, giving criminal hackers even more tools to ply their craft.
Opinion: Hacking Team breach a gold mine for criminal hackersWhile the breach at the Italian spyware firm shines a light on the shadowy world of surveillance technology, it has also made the Web a much more dangerous place, giving criminal hackers even more tools to ply their craft. Innovation at Mach 5: How defense R&D keeps America aheadWhen it comes to national security, not all research and development is created equal.
Innovation at Mach 5: How defense R&D keeps America aheadWhen it comes to national security, not all research and development is created equal. CIA documents raise questions about spy agency's domestic data collectionThe American Civil Liberties Union is concerned the CIA is collecting mass amounts of data on Americans as it conducts foreign surveillance operations.
CIA documents raise questions about spy agency's domestic data collectionThe American Civil Liberties Union is concerned the CIA is collecting mass amounts of data on Americans as it conducts foreign surveillance operations. HostGator stops sending private encryption keys in plain textThe Web hosting service had been e-mailing plain text private keys used for decrypting secure data transmitted online – a practice security experts say puts sensitive information at risk.
HostGator stops sending private encryption keys in plain textThe Web hosting service had been e-mailing plain text private keys used for decrypting secure data transmitted online – a practice security experts say puts sensitive information at risk. Opinion: Why privacy alarmists are wrong about data rules in big trade dealsProvisions in the Trade in Services Agreement, which is currently under negotiation in Geneva, are not meant to erode privacy. Instead, the pact reflects the reality of how data is stored and transmitted in the modern global digital economy.
Opinion: Why privacy alarmists are wrong about data rules in big trade dealsProvisions in the Trade in Services Agreement, which is currently under negotiation in Geneva, are not meant to erode privacy. Instead, the pact reflects the reality of how data is stored and transmitted in the modern global digital economy. Opinion: Timing is everything for securing wireless communicationsEven though disrupting wireless communications – whether cellphone networks or GPS – could harm the US economy and put lives at risk, these networks remain far too vulnerable to attacks.
Opinion: Timing is everything for securing wireless communicationsEven though disrupting wireless communications – whether cellphone networks or GPS – could harm the US economy and put lives at risk, these networks remain far too vulnerable to attacks. Why webcam indicator lights are lousy privacy safeguardsA recent academic study found that few computer users notice indicator lights and even fewer realize that the camera is always recording when the light is on. The lack of awareness, say researchers, makes people more vulnerable to webcam spying.
Why webcam indicator lights are lousy privacy safeguardsA recent academic study found that few computer users notice indicator lights and even fewer realize that the camera is always recording when the light is on. The lack of awareness, say researchers, makes people more vulnerable to webcam spying. MIT's CodePhage helps computers automatically detect, devour their own bugsMassachusetts Institute of Technology researchers presented a system to detect bugs in programs as they run and repair them by borrowing functionality from other applications.
MIT's CodePhage helps computers automatically detect, devour their own bugsMassachusetts Institute of Technology researchers presented a system to detect bugs in programs as they run and repair them by borrowing functionality from other applications. How big is Anonymous? Maybe bigger than you thoughtAn analysis from a University of Copenhagen graduate student suggests the online-phenomenon-turned-protest movement is more globally connected on the Web than previously thought.
How big is Anonymous? Maybe bigger than you thoughtAn analysis from a University of Copenhagen graduate student suggests the online-phenomenon-turned-protest movement is more globally connected on the Web than previously thought. FBI chief Comey says strong encryption diminishes agency's effortsFBI Director James Comey testified on Capitol Hill that tech companies should find a way for government investigators to access data that is encrypted on consumer devices.
FBI chief Comey says strong encryption diminishes agency's effortsFBI Director James Comey testified on Capitol Hill that tech companies should find a way for government investigators to access data that is encrypted on consumer devices. Hacking Team breach focuses attention on merchants of spywareStolen documents from the Italian firm Hacking Team provide new details into the business of selling sophisticated surveillance tools to governments and law enforcement agencies.
Hacking Team breach focuses attention on merchants of spywareStolen documents from the Italian firm Hacking Team provide new details into the business of selling sophisticated surveillance tools to governments and law enforcement agencies. The battle between Washington and Silicon Valley over encryptionTech titans are pushing back against Obama's national security officials over strong security on consumer devices, strengthened after the Snowden leaks. The outcome could impact the future of the Internet – and your privacy.
The battle between Washington and Silicon Valley over encryptionTech titans are pushing back against Obama's national security officials over strong security on consumer devices, strengthened after the Snowden leaks. The outcome could impact the future of the Internet – and your privacy. Opinion: An Underwriters Laboratories for cybersecurity is long overdueNoted security researcher Mudge left Google to launch what appears to be the cybersecurity equivalent of electronics testing outfit Underwriters Laboratories – an idea first proposed 16 years ago.
Opinion: An Underwriters Laboratories for cybersecurity is long overdueNoted security researcher Mudge left Google to launch what appears to be the cybersecurity equivalent of electronics testing outfit Underwriters Laboratories – an idea first proposed 16 years ago. How a teenage hacker might start World War IIIAn excerpt from 'Ghost Fleet,' a new novel by Peter W. Singer and August Cole, that envisions what a future global cyberconflict might look like.
How a teenage hacker might start World War IIIAn excerpt from 'Ghost Fleet,' a new novel by Peter W. Singer and August Cole, that envisions what a future global cyberconflict might look like.



