Influencers: Paris attacks don't justify government access to encryption
Loading...
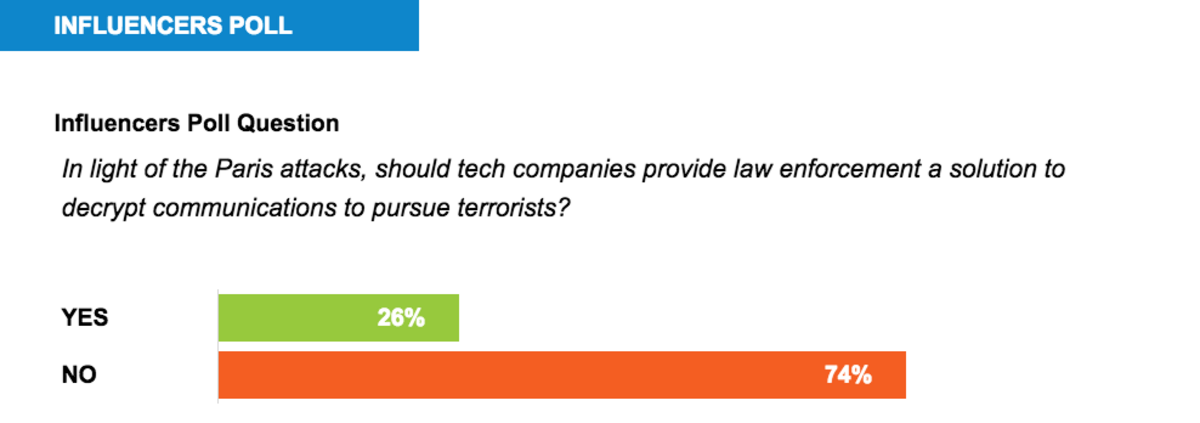
Even as the Paris attacks rekindle the encryption debate between Washington and Silicon Valley, a strong majority of Passcode Influencers said tech companies should not provide law enforcement a solution to decrypt communications to pursue terrorists.
Investigators have not yet provided concrete evidence about which platforms the Islamic State militants used to coordinate the attacks in Paris last week that killed at least 129 people. Even so, US╠²lawmakers╠²▓╣▓į╗Õ╠²╠²are already calling for greater access to strongly encrypted consumer devices and apps they complain are nearly impossible to access even with a╠²warrant.
Yet 74 percent of PasscodeŌĆÖs own pool of more than 120 experts from across the government and the private sector cautioned against a knee-jerk response to a tragedy that could give US intelligence and law enforcement agencies a power that could harm all consumersŌĆÖ security and╠²privacy.
ŌĆ£The Paris attacks are absolutely tragic, but the response must not be to undermine cybersecurity for digital services on which many millions of people depend,ŌĆØ said Harley Geiger, senior counsel at the Center for Democracy and Technology. ŌĆ£Weakening strong encryption will expose regular Internet users to increased risk of cyberattack and devastate small businesses and innovators.ŌĆØ
Giving the US government access, Mr. Geiger continued, will not prevent organized groups from using strong encryption. ŌĆ£Difficult-to-crack encryption and apps will continue to be available on the Internet, even if governments seek to ban them. Government-mandated cybersecurity vulnerabilities will do a great deal of damage, are of highly questionable effectiveness, and should not be the hasty reaction to these reprehensible terrorist attacks.ŌĆØ
After conducting an extensive policy review, the White House moved toward╠²╠²earlier this fall, to cheers from security pros and privacy advocates. Now, even as officials such as FBI Director╠²╠²in the wake of the Paris attacks, others in the government are already worried about the fate of consumersŌĆÖ security if the US moves too quickly on this╠²issue.
ŌĆ£It is important not to leap to the conclusion that mandating backdoors or exceptional access systems in commercial products is necessary,ŌĆØ said Terrell McSweeny, a commissioner at the Federal Trade Commission. ŌĆ£Experts agree that backdoors introduce security flaws and vulnerabilities. Consumers using these products may be more vulnerable if the security of them is weakened.ŌĆØ
That concern was echoed by several Influencers, who said itŌĆÖs still important to note that if law enforcement has a channel to bypass encryption, an unauthorized party also has a better chance of getting access to the╠²data.
ŌĆ£If tech companies create an encryption ŌĆśbackdoorŌĆÖ then what is the point of encrypting things in the first place?ŌĆØ said Cris Thomas (aka Space Rogue), strategist at Tenable Security. ŌĆ£If a backdoor is created, there is no way to limit access only to law enforcement or ŌĆśfriendlyŌĆÖ governments. Eventually, and sooner rather than later, the bad guys will get access to the backdoor... [and they themselves] will just evolve to use a different communications╠²method.ŌĆØ
ThatŌĆÖs a grim scenario, he said: ŌĆ£Law enforcement will still have no way to monitor the bad guys and the public will be left with weakened security.ŌĆØ
The fact that officials and policymakers are already using the attacks to revive the debate ŌĆö without a definitive answer on whether or not encryption was used by the attackers ŌĆö is especially problematic, some Influencers said. ŌĆ£At this point there is no confirmation that end-to-end encryption was used by the attackers, much less that the use of that encryption is what led the worldŌĆÖs intelligence services to fail to detect the plot before the tragedy,ŌĆØ said Cindy Cohn, executive director of the Electronic Frontier Foundation. ╠²
On the other hand, the benefits of widespread, strong encryption are well known, Ms. Cohn said. ŌĆ£What we do know is that strong encryption is crucial to allow political organizers, government officials, and ordinary people around the world to protect their security, privacy and safety from criminals and terrorists╠²alike.ŌĆØ
ŌĆ£Any ŌĆśbackdoorŌĆÖ into our communications will inevitably (and perhaps primarily) be used for illegal and repressive purposes rather than lawful ones,ŌĆØ she said.╠²
Unfortunately, said Julian Sanchez, a fellow at the Cato Institute, a libertarian think tank, the urgency policymakers feel to respond to the attacks ŌĆö and other threats the Islamic State has made against other targets, including Washington ŌĆō does not lend itself to an even-handed╠²debate.
ŌĆ£ItŌĆÖs increasingly clear that advocates for compromising encryption rushed to exploit a tragic attack in the absence of any evidence that encryption technology had actually stymied investigation of the Paris attackers,ŌĆØ Mr. Sanchez said. ŌĆ£This looks like yet another effort to scapegoat technology for an intelligence failure.ŌĆØ╠²
Despite the loud opposition from many technologists and privacy advocates, a 26 percent minority of Passcode Influencers said the Paris attacks do highlight reasons why the US government needs the ability to encrypted communications to keep the country╠²safe.
ŌĆ£They should provide as much access to securing the national defense as they do to profit making advertisers and data aggregators,ŌĆØ said one Influencer who preferred to remain anonymous. Influencers have the option to comment on the record or anonymously to preserve the candor of their responses.
The debate over balancing national security and privacy is much bigger than this one attack, some Influencers stressed. ŌĆ£The Paris events should have nothing to do with this,ŌĆØ an Influencer who preferred to remain anonymous╠²said.
ŌĆ£Under any circumstances, with due process under the law, mechanisms must exist to allow law enforcement to gain access to communications.ŌĆØ
What do you think?╠²╠²of the Passcode Influencers Poll.
╠²
Comments
NO
ŌĆ£Law enforcement ŌĆśbackdoorsŌĆÖ can be abused by attackers to decrypt traffic of victims.ŌĆØ -╠²Charlie Miller, Uber Advanced Technologies Center
ŌĆ£No. That lesson should have already been learned with the abuses of the Patriot Act post 9/11. Our rights must remain intact as we pursue and punish terrorists and other criminals.ŌĆØ -╠²Jeffrey Carr, Taia Global
ŌĆ£The risks after 13-11 remain as they were before 13-11 ŌĆō ╠²the vulnerabilities enabled by broken crypto leave consumers and companies more vulnerable to cyber attack.ŌĆØ -╠²Marc Rotenberg, Electronic Privacy Information Center
ŌĆ£Any ŌĆśsolutionŌĆÖ would fundamentally weaken encryption for everyone and introduce new risks. The focus needs to be on how to surveil specific persons in spite of strong encryption, and not weakening encryption for all so that agencies can collect information in bulk.ŌĆØ -╠²Chris Finan, Manifold Security
ŌĆ£If law enforcement have a way to decrypt communications, itŌĆÖs an opening for others.ŌĆØ -╠²John Bruce, Resilient Systems
ŌĆ£It is misleading to frame the policy discussion about crypto backdoors in the narrow context of terrorism. People who plan terrorist attacks take care to protect their schemes from discovery, and already have access to crypto systems that do not have backdoors. Technology companies are being asked to build backdoors into systems that regular people use everyday, and those backdoors would be accessed for a variety of mundane law enforcement purposes. ItŌĆÖs a complex issue that should not be oversimplified.ŌĆØ -╠²Tom Cross, Drawbridge Networks
ŌĆ£There are many ways the intelligence community can use technology to fight terrorism, but breaking encryption should not be one of them. On net, we will all be more secure over the long term if we focus on developing a more secure digital world, not a less secure one.ŌĆØ -╠²Daniel Castro, Center for Data Innovation
ŌĆ£While technology companies should, of course, cooperate fully with law enforcement officials to capture terrorists, there is no magical ŌĆśdecrypt communications only for terroristsŌĆÖ technology. Overwhelmingly, protecting the integrity of communications benefits civil society as a whole. Fools and cowards fear encryption -- they draw attention to secure communications because they are unwilling to have the far more meaningful conversations about how to stop terrorism -- including a Marshall plan for the MENA and AfPak regions that provides meaningful economic alternatives to local youth, expansion of social services to serve battered communities, and reining in of hostile action, and even gun control. We need a fundamental rethink of our failed foreign policy, not less secure communications that will inevitably make us all less safe to abuse by government authorities and hackers alike.ŌĆØ -╠²Sascha Meinrath, X-Lab
ŌĆ£It may be a legitimate function of governments to attempt to collect information for law enforcement or intelligence purposes through cryptanalysis. However, nothing in that statement should be interpreted to suggest that vendors ever intentionally weaken privacy and security measures in their products in furtherance of that end. Encryption is ŌĆ£critical infrastructureŌĆÖ in the modern online economy. One canŌĆÖt design in a weakness and ensure that ŌĆśonly good guysŌĆÖ have the ability to exploit it. The ŌĆśgolden keyŌĆÖ that only allows access to government monitors without creating any new attack surface or weakness is the stuff of fantasy, until someone arrives with as-yet unknown mathematics.ŌĆØ -╠²Bob Stratton, MACH37
ŌĆ£Suggesting that we need to sacrifice privacy in order to preserve security is a false choice. The two are not mutually exclusive.ŌĆØ -Trevor Hughes, International Association of Privacy Professionals
ŌĆ£There should be no knee jerk reactions to technology and cryptography. The Paris attacks shouldnŌĆÖt be politicized in this way; instead we should simply mourn the loss of life instead of using this as a platform to advance the debate in any one direction. The cryptography debate has been going on for a long time and we have always known that terrorists do and will use cryptography. Backdoors into encryption undermine its value and open it up to abuse. There is no ŌĆ£good guy backdoorŌĆØ and even if there was there is no evidence that doing so would actually result in more identification and prosecution of terrorists. Even in the case of the Paris attacks there were multiple aspects of information sharing, coordination, and traditional intelligence analysis that could have been done to identify warning signs. The problem with governmentŌĆÖs not identifying terrorists is not an issue of technology but an issue of the challenges towards intelligence in modern day society. There is an overvaluing of Intelligence towards this problem when there are other aspects of statecraft that must be engaged to stem violent radicalism. Simply put, Intelligence is not to blame and any failures in Intelligence are more likely to be the result in processes and bureaucracy not technology.ŌĆØ -╠²Robert Lee, Dragos Security
ŌĆ£I disagree with the premise of the question. I have yet to see a credible story linking the Paris attacks to any use of encryption.ŌĆØ -Influencer
ŌĆ£This question is hard to answer as constructed. If presented with duly approved legal requests, companies should provide decrypted information - if they are able to do so. Companies should not, however, be compelled to build in backdoors for the benefit of government intelligence gathering.ŌĆØ -╠²Influencer
ŌĆ£Adding a backdoor is a giant sword that cuts both ways.ŌĆØ -╠²Scott Montgomery, Intel Security
ŌĆ£We should not be giving up our right to privacy because a terrorist kills someone. ThatŌĆÖs what terrorism is - it scares people into making irrational decisions. It is exactly what they want. They want us to give up our freedoms and overreact. ItŌĆÖs a dangerous precedent weŌĆÖre giving our enemies, ŌĆśAttack us and weŌĆÖll tighten our noose on our own people, give you better attack points, and lessen their ability to protect themselves.ŌĆÖ ItŌĆÖs just a terrible idea to make an irrational decision out of fear.ŌĆØ -╠²Influencer
ŌĆ£In our digital world, the use of encryption is intertwined with the ability to exercise our human rights. Now, more than ever, we must defend those rights and our freedom to exercise them.ŌĆØ -Amie Stepanovich, Access
ŌĆ£Government-required backdoors of large tech companies will not stop peer-to-peer encryption efforts by criminal and terror organizations. They can make their own way. Most large tech companies generally operate for the common good when asked by governments to make information available in special circumstances without being forced to do so by law.ŌĆØ -╠²Influencer
ŌĆ£A bad idea doesnŌĆÖt improve with less time to consider it.ŌĆØ -╠²Nick Selby, StreetCred Software
ŌĆ£If such a system in place, terrorists will switch to alternate communications mechanisms, resulting in zero benefit to law enforcement. A better approach is a combination of ŌĆśold fashioned police work,ŌĆÖ eliminating the funding sources of terrorism, and eliminating the root causes of radicalization.ŌĆØ -╠²Influencer
ŌĆ£Even if tech companies gave law enforcement a backdoor to decrypt communications, motivated terrorists could find a way to communicate without depending on these tech companies.ŌĆØ -╠²Yan Zhu, security engineer
ŌĆ£This *will not fix the problems*. TheyŌĆÖll use non-regulated crypto. Meanwhile, innocent Internet users everywhere will have their security and privacy violated.ŌĆØ -╠²Influencer
ŌĆ£We have to give law enforcement the tools it needs to detect and disrupt terrorists and criminals. But rushing ahead could do more harm than good. The reality is we cannot protect these ŌĆ£backdoorsŌĆØ or special ŌĆ£keysŌĆØ. In essence, we would be leaving the backdoor unlocked not just for law enforcement, but terrorists, and cyber criminals.ŌĆØ -╠²Jenny Durkan, Quinn Emanuel
ŌĆ£First off, we shouldnŌĆÖt be rushing to make changes without even knowing if this played a role. Second, the reason the administration ultimately backed down from Jim ComeyŌĆÖs push on this front is that all technologists agreed there was no such feasible solution. Thus, we need to take a deep breath and simultaneously recognize that sometimes global technologies can overcome our policy predelictions.ŌĆØ -╠²Influencer
ŌĆ£I take the question to be not whether companies should be responsive to warrants -- if they fall under a governmentŌĆÖs jurisdiction, theyŌĆÖll have to be, adjusting for whatever options for legal objection they may have. The real question is whether companies should be prevented from designing products and services that happen to deprive the companies themselves of the ability to see what their users are doing. And that, for both practical and theoretical reasons, is not a requirement that companies should have to undertake. A lot of my reasoning on this is spelled╠²].ŌĆØ -╠²Jonathan Zittrain, Harvard Law School
ŌĆ£The effort to relitigate this issue because of Paris is foolishness.ŌĆØ -Jim Harper, Cato Institute
ŌĆ£Terrorism is horrible. But we are worse off with no encryption.ŌĆØ -Influencer
ŌĆ£The terrorist attacks on Paris are a terrible tragedy. Without question policy makers should make sure law enforcement has the right tools and resources to track down terrorists and stop them. It is important not to leap to the conclusion that mandating backdoors or exceptional access systems in commercial products is necessary. Experts agree that backdoors introduce security flaws and vulnerabilities. Consumers using these products may be more vulnerable if the security of them is weakened. Moreover, in an environment where there are plenty of open-source encryption options, it is unlikely that mandating backdoors on commercial products and major platforms will stop bad actors from using open-source programs, legacy technologies, or even their own products to hide their communications.ŌĆØ -╠²Terrell McSweeny, Federal Trade Commission
╠²
╠²YES
ŌĆ£When national security matters dictate, it requires a strong public/private partnership to mitigate threats and save lives.Sharing cybersecurity capabilities should be part of that partnership.ŌĆØ -╠²Chuck Brooks, Sutherland Global Services
ŌĆ£The Paris events should have nothing to do with this. Under any circumstances, with due process under the law, mechanisms must exist to allow law enforcement to gain access to communications.ŌĆØ -╠²Influencer
ŌĆ£This is a very difficult question, with serious policy and political issues arising from however one answers. There is the old legal aphorism, that ŌĆ£hard cases make bad law,ŌĆØ and this is certainly a hard case. But we are dealing with an implacable threat, which has shown no reluctance or mercy in attacking a wide range of ŌĆśsoft targets;ŌĆÖ what if ISIS or another islamic terrorist groups acquires a WMD? Surely they would not hesitate to use it, with catastrophic consequences for the targeted area. In the aftermath of such a disaster, the least weŌĆÖll be talking about is giving LE access to encrypted systems. IŌĆÖd rather we are never faced with such a HobsonŌĆÖs Choice, but keeping the terrorists on the defensive and ultimately defeating them, rather than cleaning up after another devastating attack.ŌĆØ -╠²Influencer
ŌĆ£I would have answered the same way before the Paris attacks. I do not believe we want to live in a world where criminals are given guaranteed safe spaces to conduct their planning. We have never built cars with trunks that cannot be opened by law enforcement with a search warrant. After 9-11 you can lock your luggage but only with a lock that allows TSA access. Why are cell phone communications different? Reasonable people can disagree, but I am more concerned about the threat from terrorists and criminals than I am concerned about the NSA surveilling me.ŌĆØ -╠²Influencer
ŌĆ£This was a legitimate concern before the attacks and the issue has created greater urgency. National security is an inherently governmental responsibility and the governmental must have access to this information with appropriate safeguards.ŌĆØ -Influencer
ŌĆ£If the provider has a key, they should be required to provide it under law. But they should not be REQUIRED to create such a key. It is pointless to try to legislate against scientific progress.ŌĆØ -Influencer
ŌĆ£Within a legal framework that is transparent to the American people.ŌĆØ -╠²Influencer
ŌĆ£I think that decryption technology, used correctly and legally, is perfectly appropriate for defeating nefarious actors. Personally, IŌĆÖm willing to give up a little privacy control for a safer world.ŌĆØ -Influencer
ŌĆ£While I respect privacy rights, this is an opportunity to build an adequate legal framework for counterterrorism in the digital age.ŌĆØ -╠²Influencer
ŌĆ£They should provide as much access to securing the national defense as they do to profit making advertisers and data aggregators.ŌĆØ -╠²Influencer
What do you think?╠²╠²of the Passcode Influencers Poll.
╠²